Our phone has been keeping our lives within it. And it is not an exaggeration – you load information into it and give full access. Bank accounts and transactions, personal photos, conversations and even your place of residence – all these data are stored in a small, simple device – your smartphone. Not surprisingly, this abundance of easily accessible information can attract hackers or other attackers.
Attackers often take advantage of the fact that people are not aware of official sources. Thousands of people still download social networking apps and messengers from unofficial sources, not to mention visiting malicious sites.
The average person who sees the name “security” or “safety” downloads files from this site without hesitation. Thousands of smartphones were hit by malware in 2017 because of this trick.
We believe you came across this article in search of a way to secure your data. In our opinion, it is better to start with the basics of studying the problem and consider what types of threats exist on the Internet for your technology.
Types of threats and hacking techniques
1. Phishing links
The easiest and most accessible way for villains is to send out phishing links. Attackers send a huge number of emails and SMS with malicious links to suspicious sites. Often these emails are signed ” Look at the pictures” or “Here is the video from the last corporate party”. A person opens a link without suspicion and downloads a malicious program to his device, which immediately begins its work.
Sometimes sites use a similar system. They redirect you to another source, where you download what you were looking for. However, with a small correction: the file you need will be attached to another, very small file – but it will start to interfere with you.
You can also receive SMS on behalf of your bank – obviously, fraud. There may be requirements to enter a password for your card or to send any other bank data – such SMSs are among the most dangerous. With their help cheaters can get access not only to your phone, but also to bank accounts.
2. SS7 signaling protocol
All people have a personal right to privacy of correspondence and conversations. But have you ever had the feeling that someone else is present when you talk on your mobile phone? You may even have heard someone else breathing or interfering during the conversation, in which you could distinguish a stranger (or even a few people!).
It is quite possible that this is not a paranoia and hallucinations you are having, but real people. According to the law, security services, telephone companies and even other people are not allowed to access your line of communication. But it happens that someone bypasses the law and still eavesdrops on your conversations.
This is a relatively easy offense to commit: an intruder connects to SS7 and indicates your number as a home number. Thus, often intercepted calls and SMS from high-ranking officials, big businessmen or just influential people.
Although in most cases you have nothing to worry about – such attacks are carried out in most cases on famous people – the attackers simply do not care about how you talk to your friends or your dog’s veterinarian.
3. Applications – spies
Such applications are no longer installed by your own naivety or stupidity. As sad as it may sound, this software can be installed on your smartphone by people you trust. In this case, everything happens as follows: the intruder gets your phone for just a few minutes.
During this time he installs the necessary programs – for example, Spy Phone App or Spyera. They implement a real surveillance, so complete that the level can be compared only with the intelligence services.
Such applications intercept and record your calls and SMS, the complete history of search queries and website visits. Such applications send to the person who has established to you his information on your movements and even activity in social networks. Thus, all correspondence from WhattsApp and Facebook will be in the hands of an intruder.

4. Open Wi-Fi networks
Probably the easiest and most obvious way to break in. Every time you connect to a Wi-Fi network at an airport or cafe, you show all people your traffic. It is not encrypted and is really easily accessible to any person who will show interest.
Not so long ago, there was a major scandal in Russia: an ordinary passenger was able to view all the data on the accounts, as well as the search history of other passengers on the train.
For such negligence and lack of safety it is your sole responsibility to be aware because none of the company’s representatives guarantees you confidentiality in an open Wi-Fi network and you voluntarily connect to it.
You may also like: 11 Best Private browser apps for Android & iOS
The main signs that your smartphone has been hacked
1. “Independent” phone life
You may have noticed that some features of your smartphone are constantly enabled and disabled without your participation. For example, the definition of GPS, Bluetooth or even the mobile Internet.
This means that there is something wrong with your smartphone – it is possible that some of its functions have already been taken over by a malicious application.
2. Battery heating
All smartphones and tablets are affected by heat. However, this is usually the case with active use, such as downloading a game or running multiple applications at the same time.
In the case of hacking, your smartphone can be heated even at rest. If you suddenly notice that even when you don’t use the device, the battery is still hot – it means that there is a program running in your smartphone.

3. Quick loss of battery power
Heating alone may not always be the only sign that other applications are working. If your smartphone has always stored a battery charge for a long time and has recently started to run out of power, you can be sure that an external application is constantly running. Of course, you may have forgotten to close any programs, but if this situation repeats itself, you should be warned.
4. Unknown numbers in the call log
Sometimes malicious software is designed to be beneficial. All over the world there is such practice as paid calls and SMS. The received funds go to the account of the subscriber you are calling or writing to. Some programs deal with this type of fraud.
The virus makes paid calls to certain numbers, but they also appear in your call log. After you find the numbers, check the balance of your SIM card – if there are less funds than you expected, you should be careful.
5. New applications
We all know that in the App Store and Google Play the popularity of applications is determined by the number of downloads. Some unscrupulous developers use fraudsters to increase the popularity of their products.
The virus that appears in your smartphone starts downloading any new applications to your smartphone. This impact is easy to see, so you will immediately notice that there is a “replenishment” of the apps in your memory.
6. Echoes or strange sounds during conversations
This feature is typical of when you begin to feel that you have been intercepted in your conversations. Many aspects can be attributed to poor cellular communication or interference on the line, but it can also be a sign of your smartphone hacking.
As we have already mentioned, such problems are more associated with popular people and usually cybercriminals want to get their calls but everything is possible. Have you suddenly started to hear strange voices, sounds or echoes during your phone calls? This is a reason to think about it!
7. Advertisements
Advertising banners and pop-up windows can be called the most popular and most obvious sign of a break-in of your smartphone. Usually these are either regular ads or short video clips of 5-10 seconds duration.
Advertising content is aimed at distributing new games or sites that you can go to after watching. In fact, this virus is very harmless, but pop-up windows can be annoying or can appear at the wrong time. In this case, you can immediately detect hacking or malware on your smartphone.

8. Blocking the antivirus features
Sometimes when you buy a phone you may find that it already has an anti-virus program installed. You may even have installed it yourself for security reasons. Anti-viruses always send notifications to users – about detection of suspicious programs, new files or even viruses of high quality.
The most modern viruses block the action of protective programs, but antiviruses can still send you notifications. Even when the protection fails to cope with the attack, you will know about it and will be able to take timely measures to save your data.
You may also like: 11 Best Phone Virus Cleaners for Android & iOS
What do you do if you find your smartphone hacked?
When no antivirus has been installed on your smartphone, it is time to do so. If you suspect the presence of malicious software or even believe it is present, the protection apps will help you get rid of it and put your smartphone back into normal operation. We offer you some of the most popular and proven options that you can easily install on your smartphone.
Avast SecureLine VPN Proxy
 Avast is a popular antivirus that you can install on your smartphone as well as on your computer. Most importantly, it not only performs the functions of antivirus, but also protects your information. For example, if you connect to an insecure Wi-Fi network, the application creates a private VPN link that allows you to easily connect to any network without risk of data loss.
Avast is a popular antivirus that you can install on your smartphone as well as on your computer. Most importantly, it not only performs the functions of antivirus, but also protects your information. For example, if you connect to an insecure Wi-Fi network, the application creates a private VPN link that allows you to easily connect to any network without risk of data loss.
You can also choose your own location to avoid tracking. Since Avast is covered all over the world, you can easily change from “United States” to “Norway”. Since your communication will be protected, no one will receive your personal data.
More than 400 million people have already trusted Avast and you can become one of them. Subscribing to the service is much cheaper than losing your personal correspondence or bank statements.

Lookout
 Lookout is a universal application that combines almost all the functions of antivirus. In addition to protection, you get an almost personal assistant who will do everything possible to minimize damage in an emergency.
Lookout is a universal application that combines almost all the functions of antivirus. In addition to protection, you get an almost personal assistant who will do everything possible to minimize damage in an emergency.
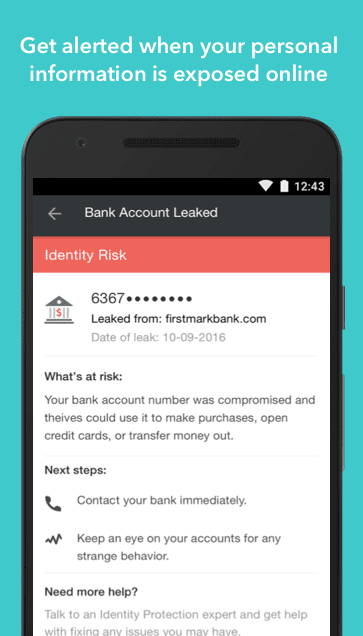
If the application detects malware or data leakage, it alerts you immediately. Even if the company you are using suffers from a data breach, you will also be informed.
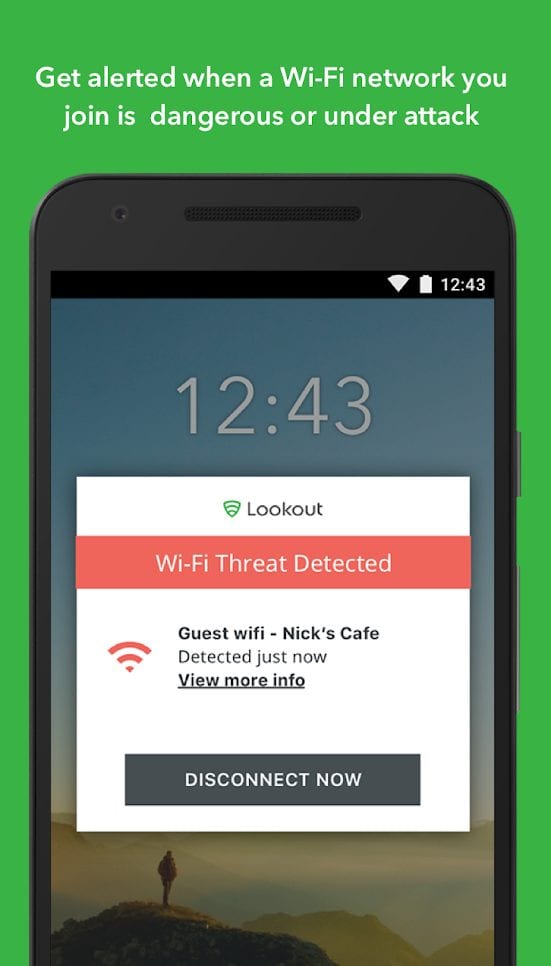
Lookout also protects your traffic: you can connect to open Wi-Fi hotspots without fear, and you won’t be exposed to phishing attacks. There is a Premium Plus subscription version that becomes your protector in almost every sense.
For example, your data will have real insurance – up to 1 million U.S. dollars, and in case of loss of a real wallet Lookout will contact your bank and suspend the cards.
You will also be able to quickly cancel and recover lost documents – isn’t this a real helper function?
Clean Master
 This application has been installed by users more than 1 billion times – do you have any idea how many devices have been protected by Clean Master? With it you not only protect your device, but also optimize its operation.
This application has been installed by users more than 1 billion times – do you have any idea how many devices have been protected by Clean Master? With it you not only protect your device, but also optimize its operation.
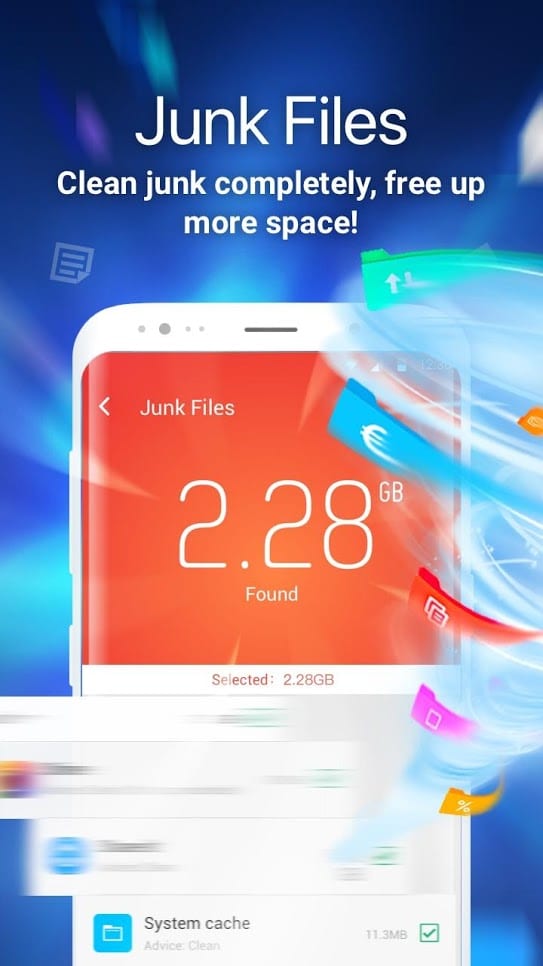
Of course, bugs and delays can be caused by malware, but there are other factors to remember. A Clean Master can really speed up your device and clear your memory of unnecessary garbage. This is done by clearing the RAM and removing unnecessary tasks.
The application also analyzes your files and if you don’t use them – Clean Master offers to delete unnecessary ones. And of course, security. The application analyzes your smartphone, all programs and files stored in it.
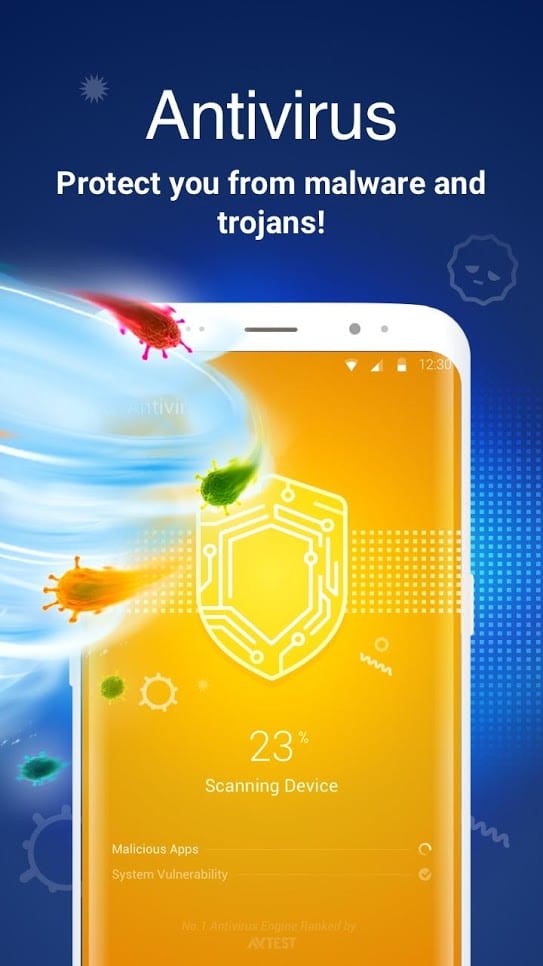
Clean Master will help you to uninstall malicious programs without any trace, as well as not to install anything new from unconfirmed sources. We think that a huge database of users and positive feedback will remove your doubts completely.
If you were able to find an application that steals your data or controls your smartphone yourself, you can solve the problem. You will need to go to your phone settings, open the entire list of installed applications, and remove the one you think is suspicious.
In particularly complex cases, you can reset your smartphone to the factory default settings. This way, you can delete all your files, both malicious and your entire collection of photos and other documents.
No unpleasant situations will happen to your data if you follow a few simple recommendations:
1. Never install applications from other sources. All of the apps and their equivalents can be found in the App Store or Google Play, especially since they have already passed the security check.
2. Try not to connect to open Wi-Fi networks. You should also disable the automatic connection to available Wi-Fi networks, so you better manually select the access points you can connect to.
3. In no case, do not open links or download files that are sent to you by an unknown source. The same applies to links that you don’t see the full name of – they can be harmful to your smartphone.
4. A little more about open Wi-Fi networks. Don’t shop when you connect to them – this can give attackers the opportunity to steal your bank details or even money.
5. And, of course, be vigilant. If you install a good antivirus on your smartphone and scan periodically, you will definitely avoid unnecessary attacks.
We hope that our article was really useful for you. If you find one of the signs of hacking in your smartphone – do not hesitate, try to solve the problem as soon as possible to avoid data theft.